Kubernetes(K8s) - The Power of Service Mesh - Istio
In today’s world, most applications are built using microservices — small, independent services that work together to create a larger system. While microservices
offer many benefits, they also bring challenges:
How do services communicate securely?
How can we monitor and control traffic between services?
How do we make sure our system is reliable and scalable?
This is where a Service Mesh comes in. A service mesh is a layer that manages communication between microservices, making it easier to handle security, traffic control,
and monitoring. Instead of adding this logic to each service, the service mesh takes care of it automatically.

Why Istio?
Istio is one of the most popular service mesh solutions. It helps developers by:
- Managing traffic — Control how requests flow between services.
- Improving security — Encrypting traffic and handling authentication.
- Adding observability — Monitoring and tracing service behavior.
In this blog, we’ll explore how Istio works, its key features, and how to set it up in Kubernetes. Whether you’re new to service
meshes or looking to level up your skills, this guide will help you get started with Istio.
To understand and experiment with Istio, we first need a microservices-based application that we can deploy and manage using a service mesh.
For this blog, we will use a BookInfo System, a real-world example that consists of multiple microservices working together. Below is its design:
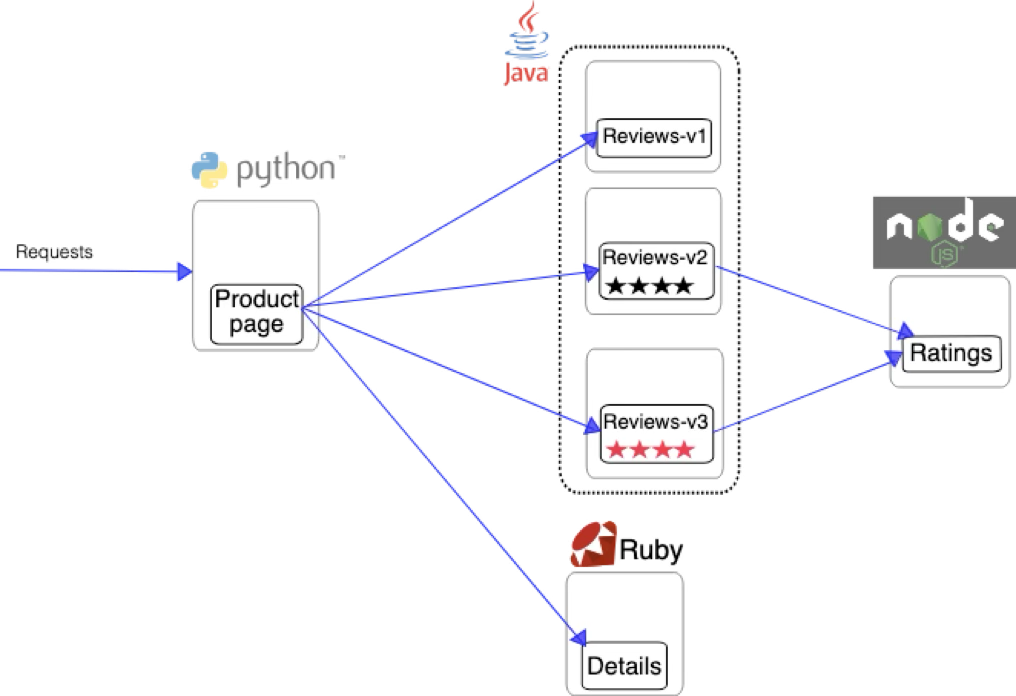
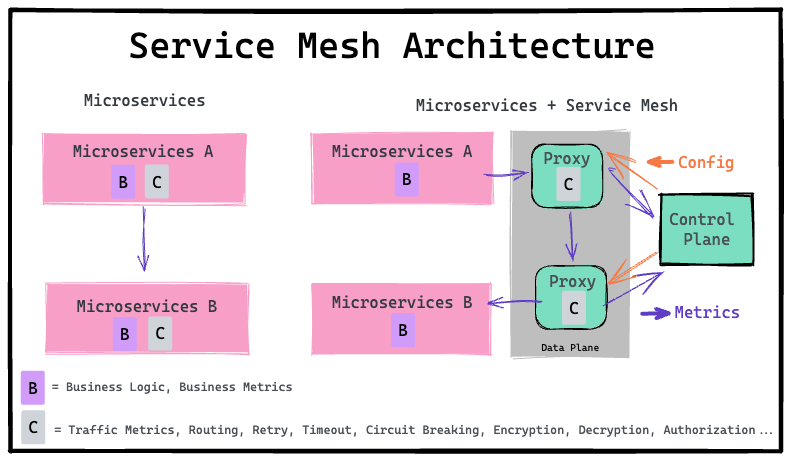
What is a service mesh ?
A service mesh is an infrastructure layer that manages service-to-service communication in microservices architectures, offering features like traffic routing,
load balancing, service discovery, and security through mutual TLS (mTLS). It enhances observability with metrics, logging, and distributed tracing while improving
resilience with mechanisms like retries, failovers, and circuit breakers. Service meshes, such as Istio, Linkerd, or Consul Connect, use lightweight sidecar proxies
(e.g., Envoy) deployed or proxies ate node level called ambient proxies alongside each service to handle network traffic transparently, enabling advanced functionality
without requiring changes to application code.
This is particularly valuable in large-scale, complex systems where managing service communication manually is inefficient.
Istio supports two main data plane modes:
sidecar mode, which deploys an Envoy proxy along with each pod that you start in your cluster, or running alongside services running on VMs.
ambient mode, which uses a per-node Layer 4 proxy, and optionally a per-namespace Envoy proxy for Layer 7 features.
We will try Ambient Mode as an example in our blog.
Download & Install
Istio is configured using a command line tool called istioctl. Download it, and the Istio sample applications:
curl -L https://istio.io/downloadIstio | sh -
cd istio-*
export PATH=$PWD/bin:$PATH
istioctl version
istioctl install --set profile=ambient --skip-confirmation
Kubernetes Gateway API CRDs do not come installed by default, so make sure they are installed before using the Gateway API:
kubectl apply -f https://github.com/kubernetes-sigs/gateway-api/releases/download/v1.3.0/standard-install.yaml
Deploy the BookInfo App with Gateway
Deploy the bookinfo App along with gateway using below commands:
kubectl apply -f bookinfo.yml
kubectl apply -f bookinfo-version.yml
kubectl get pods
kubectl apply -f bookinfo-gateway.yml
kubectl annotate gateway bookinfo-gateway networking.istio.io/service-type=ClusterIP —namespace=default
kubectl get gateway
kubectl port-forward svc/bookinfo-gateway-istio 8080:80
curl -kp http://localhost:8080/productpage
You must be able to access Web Application using Curl or Browser.
All this code is avilable at GitHub Repo
Enable Ambient Mode
To adds Pods of one Namespace to Istio, we need to label Namespace as follows:
kubectl label namespace default istio.io/dataplane-mode=ambient
Now, lets create another Pod in the same Namespace and test connection to BookInfo Service.
kubectl apply -f curl.yml
kubectl exec deploy/curl -- curl -s "http://productpage:9080/productpage"
Above commands will give HTML Code of BookInfo App as curl Pod must be able to access it.
Ambient Mode - Layer 4 Authorizations
Istio's Layer 4 (L4) authorization policies allow you to control access to and from services based on workload identities within the mesh,
using the ztunnel proxy in both sidecar and ambient modes. This provides a way to enforce network-level access control at the connection level.
Now, lets deploy layer 4 Authorizations to make BookInfo App accessible only from Gateway as follows:
apiVersion: security.istio.io/v1
kind: AuthorizationPolicy
metadata:
name: productpage-ztunnel
namespace: default
spec:
selector:
matchLabels:
app: productpage
action: ALLOW
rules:
- from:
- source:
principals:
- cluster.local/ns/default/sa/bookinfo-gateway-istio
Now, lets deploy Layer 4 Authorizations Policy.
kubectl apply -f m4policy.yml
It's time to test the Policy by hitting BookInfo URL from curl Pod.
kubectl exec deploy/curl -- curl -s "http://productpage:9080/productpage"
As you verify above, the curl Pod is NOT able to access WebPage of BookInfo as Layer 4 Policy disables acess to it.
Istio - Traffic Management
Using Istio HTTP Route, we can control traffic to specific Service. Let’s configure traffic routing to send 90% of requests to reviews v1 and 10% to reviews v2 as follows:
apiVersion: gateway.networking.k8s.io/v1
kind: HTTPRoute
metadata:
name: reviews
spec:
parentRefs:
- group: ""
kind: Service
name: reviews
port: 9080
rules:
- backendRefs:
- name: reviews-v1
port: 9080
weight: 90
- name: reviews-v2
port: 9080
weight: 10
Now, lets deploy traffic policy
kubectl apply -f traffic.yml
It's time to test the Policy by hitting BookInfo URL. Make sure you deleted Layer 4 Authorizations while performing this.
kubectl exec deploy/curl -- sh -c "for i in \$(seq 1 100); do curl -s http://productpage:9080/productpage | grep reviews-v.-; done"
As you verify above, the most requests goes to reviews-v1 as per traffic policy.
Summary and Conclusions
This highlights how Kubernetes and Istio together create a scalable and secure microservices architecture. Kubernetes manages the deployment and scaling of services, while Istio enhances traffic management, security, and observability. With these tools, we ensured smooth updates, improved reliability, and built a system ready for future growth.
Author

Sagar Mehta is Atgen Software Solutions Founder and a recognised expert in the field of Intelligent Automation, including Robotic Process Automation, Workload Automation, DevOps, SRE and Advanced Analytics. Sagar advocates a pragmatic approach to Automation, encouraging a policy of using ‘the best tool for the job’.
Prior to co-founding Atgen Software Solutions, Sagar worked in Senior Automation roles, architecting and delivering robust, scalable solutions for many of the world’s biggest banks and working with leading Automation vendors. He developed his first automated solution in 2006 and has continued to deliver robust, scalable and sophisticated Automation ever since.
Sagar is a regular guest speaker and panellist at Automation seminars, conferences and user group events.
Contact
Have a similar problem to solve, let's work together.
Our Address
#107, Tower B, Escon Arena, Zirakpur, Punjab, India - 140603
Email Us
info@atgensoft.com
Call Us
+91-8806666141
