Azure Entra ID(AD) User with Terraform
Microsoft Entra ID (previously Azure active directory) is an enterprise identity service that manages your organization's user lifecycle. The Entra ID Terraform provider lets organization administrators manage users, groups, service principals, and applications as code. Terraform provides several benefits over using the Azure Portal to manage your organization's Active Directory like safety, consistency and improved automation. In this tutorial, you will create new users in your Entra ID:
Step 1
Go through each step in Configuring a User or Service Principal for managing Azure Active Directory
Step 2
In the Azure Portal, navigate to "Azure Active Directory", then click "App Registrations". Click your Service Principal (or create "New Registration").
Step 3
Under "Essentials", copy client_id and tenant_id.
- Application (client) ID: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
- Directory (tenant) ID: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
Step 4
Navigate to your configuration (e.g., main.tf). Pass your client_id, tenant_id, client_certificate_path and client_certificate_password as the AzureAD provider to use them like this:
provider "azuread" {
client_certificate_path = var.client_certificate_path
client_id = var.client_id
tenant_id = var.tenant_id
client_certificate_password = var.client_cert_password
}
Step 5
Navigate back to your Service Principal in the Azure Portal and click "API Permissions" . You want to see User.ReadWrite.All, Group.ReadWrite.All and Directory.Read.All under Microsoft Graph. If you do not see this permission you must add it by clicking "Add a permission", then "Microsoft Graph", "Application permissions", and search for "Group.ReadWrite.All", "User.ReadWrite.All" and "Directory.Read.All" (see Azure Portal screen capture below).
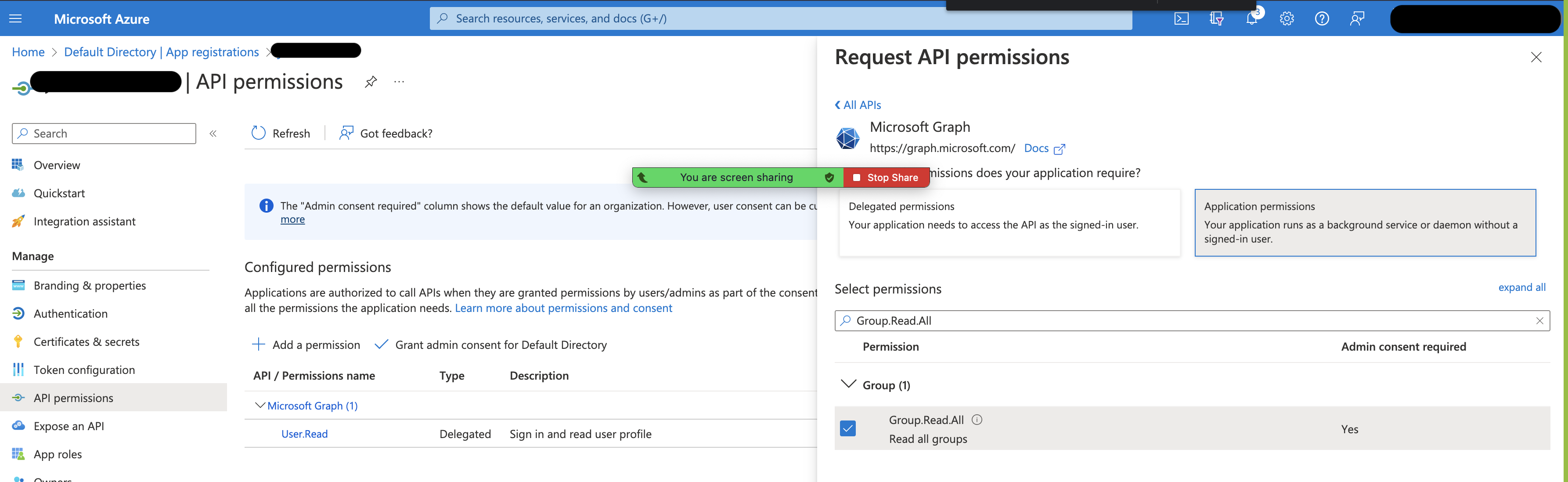
Step 6
Now you must grant consent. Just above the permission names, you will see a button "Grant Admin Consent for XXX", click that button and confirm (see Grant consent below).
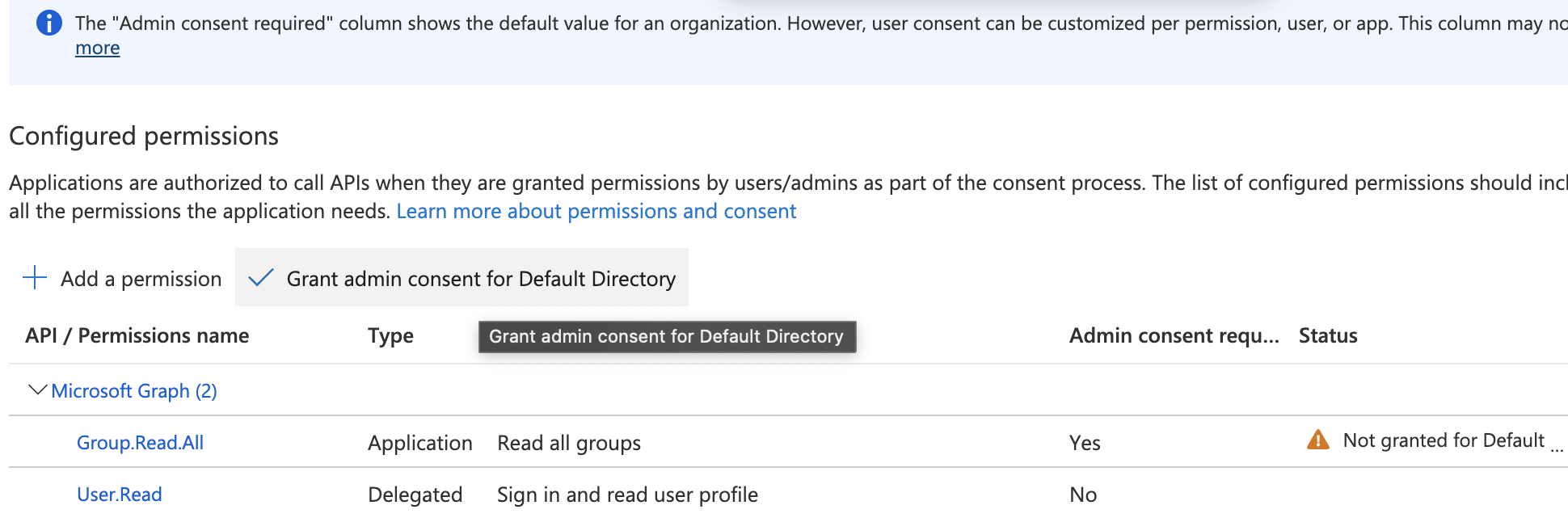
Step 7
Write Terraform code in main.tf as follows:
var "client_certificate_path" {
description = "To pass client_certificate_path with terraform command line arguments"
}
var "client_certificate_password" {
description = "To pass client_certificate_password with terraform command line arguments"
}
var "client_id" {
description = "To pass client_id with terraform command line arguments"
}
var "tenant_id" {
description = "To pass tenant_id with terraform command line arguments"
}
resource "azuread_user" "example" {
user_principal_name = "userid@domainname"
display_name = "Test User"
mail_nickname = "userid"
password = "SecretP@sswd99!" #do secure password
}
Step 8
Run below Terraform commands to create user on Azure AD:
terraform init
terraform apply --var=client_certificate_path="PFX_FILE_PATH" --var=client_certificate_password="CLIENT_CERT_PASS" --var=client_id="CLIENT_ID" --var=tenant_id="TENANT_ID"
Summary and Conclusions
You can refer the complete code at Azure AD User Create
Author

Sagar Mehta is Atgen Software Solutions Founder and a recognised expert in the field of Intelligent Automation, including Robotic Process Automation, Workload Automation, DevOps, SRE and Advanced Analytics. Sagar advocates a pragmatic approach to Automation, encouraging a policy of using ‘the best tool for the job’.
Prior to co-founding Atgen Software Solutions, Sagar worked in Senior Automation roles, architecting and delivering robust, scalable solutions for many of the world’s biggest banks and working with leading Automation vendors. He developed his first automated solution in 2006 and has continued to deliver robust, scalable and sophisticated Automation ever since.
Sagar is a regular guest speaker and panellist at Automation seminars, conferences and user group events.
Contact
Have a similar problem to solve, let's work together.
Our Address
#107, Tower B, Escon Arena, Zirakpur, Punjab, India - 140603
Email Us
info@atgensoft.com
Call Us
+91-8806666141
